The internet is evolving, and Web3 is at the forefront of this change, promising a more secure and decentralized online experience.
Beyond its association with cryptocurrency, Web3 encompasses a broader vision of decentralized infrastructure that empowers users with greater control over their data and identity.

This emerging paradigm leverages blockchain technology to enable self-sovereign identity, where individuals have autonomy over their personal data, and decentralized storage solutions that challenge traditional centralized models.
Key Takeaways
- Web3 represents a new internet paradigm focused on decentralization and user empowerment.
- Self-sovereign identity gives users control over their personal data.
- Decentralized storage solutions offer an alternative to centralized cloud storage.
- Token-gated access is revolutionizing how we manage permissions and access.
- The integration of blockchain technology is key to Web3’s decentralized infrastructure.

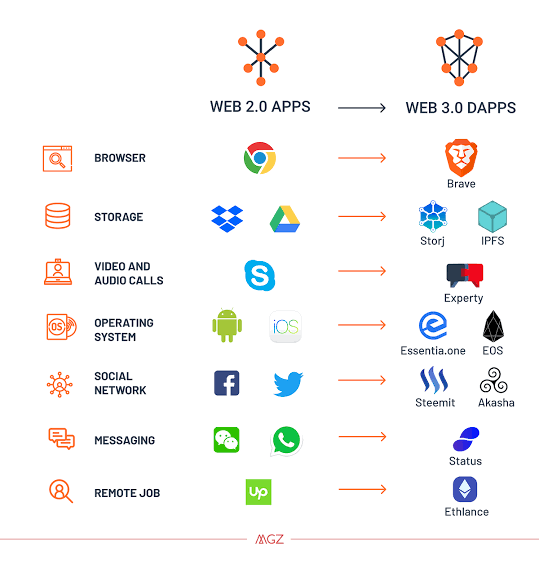
The Evolution from Web2 to Web3
Web3 represents a new era in the evolution of the internet, moving beyond the limitations of its predecessor, Web2. The current internet model, Web2, is characterized by centralized services that control user data and interactions.
The Limitations of Centralized Web2 Models
Centralized Web2 models have several limitations, including:
- Lack of user control over personal data
- Vulnerability to censorship and data breaches
- Dependence on intermediaries for transactions and interactions
These limitations highlight the need for a more decentralized approach, which is where Web3 comes into play.
The Core Principles of Web3
Web3 is built on the principles of decentralization, privacy, and user sovereignty. It enables decentralized identity management, allowing users to control their digital identities without relying on centralized authorities.
Key Technological Shifts Enabling Decentralization
The transition to Web3 is facilitated by key technological shifts, including the adoption of blockchain technology. Blockchain provides a secure, transparent, and decentralized ledger for transactions and data management, which is crucial for achieving web3 decentralization.
A comparison between Web2 and Web3 reveals significant differences in their underlying architectures and philosophies, with Web3 offering a more secure, user-centric internet experience.
Web3 Decentralized Infrastructure: Foundational Elements
Web3’s promise of a decentralized future relies heavily on the robustness of its underlying infrastructure. This infrastructure is multifaceted, comprising several key components that work in concert to provide a secure, transparent, and user-centric internet.

The Blockchain Foundation
The blockchain is the cornerstone of Web3, providing a decentralized, immutable ledger that records transactions and data across a network of computers. This technology is pivotal in ensuring transparency, security, and trustlessness in Web3 applications.
Consensus Mechanisms
Consensus mechanisms are critical in blockchain technology, enabling the network to agree on the state of the blockchain. Proof of Work (PoW) and Proof of Stake (PoS) are two of the most prevalent consensus algorithms, each with its own set of advantages and challenges.
Smart Contract Platforms
Smart contracts, self-executing contracts with the terms of the agreement written directly into code, are a fundamental aspect of Web3. Platforms like Ethereum have pioneered the use of smart contracts, enabling the creation of decentralized applications (dApps) that run autonomously.
Beyond Cryptocurrencies: A New Internet Architecture
Web3 decentralized infrastructure goes beyond cryptocurrencies, aiming to create a new internet architecture that is more resilient, secure, and user-centric. This involves not just financial transactions but also decentralized storage, identity management, and more.
The Interoperability Challenge
One of the significant challenges facing Web3 is interoperability – the ability of different blockchain systems and applications to communicate and work together seamlessly. Achieving interoperability is crucial for the widespread adoption of Web3 technologies.

| Component | Function | Examples |
|---|---|---|
| Blockchain | Decentralized, immutable ledger | Bitcoin, Ethereum |
| Smart Contracts | Self-executing contracts | Ethereum, Solana |
| Consensus Mechanisms | Network agreement on blockchain state | PoW, PoS |

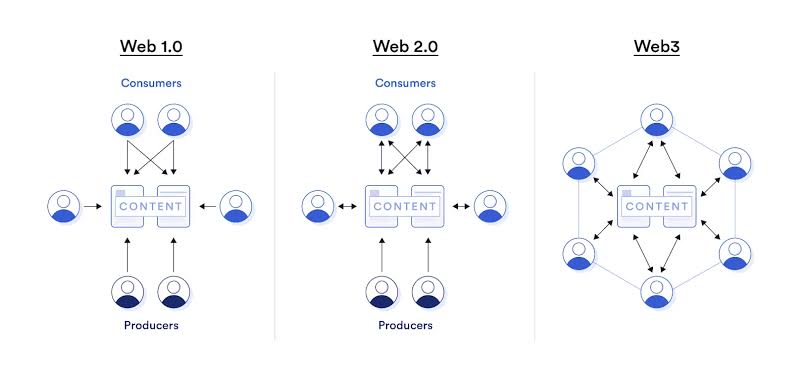
Centralized vs. Decentralized Models: A Comprehensive Comparison
Understanding the dichotomy between centralized and decentralized models is essential for navigating the future of the internet. As the digital landscape evolves, the differences between these two paradigms become increasingly significant.
Data Ownership and Control
In centralized models, data is controlled by a single entity, whereas decentralized models distribute data ownership among users. Decentralized identity management allows individuals to store and control their identities independently, without the oversight of central authorities.
This shift towards decentralization empowers users with greater control over their personal data. For instance, in a decentralized system, users can manage their data through cryptographic keys, ensuring that their information remains private and secure.
Security and Vulnerability Profiles
Centralized systems are more vulnerable to single-point attacks, whereas decentralized systems distribute risk across the network. Decentralized networks are more resilient to attacks because there is no single point of failure.
| Characteristics | Centralized | Decentralized |
|---|---|---|
| Data Control | Single entity control | Distributed among users |
| Security | Vulnerable to single-point attacks | More resilient due to distributed risk |
| Economic Model | Centralized revenue streams | Decentralized incentive structures |
Economic Models and Incentive Structures
Fee Structures and Value Capture
Decentralized models often incorporate token-based economies, where participants are incentivized through token rewards. This contrasts with centralized models, which typically rely on traditional revenue streams.
Network Effects and Moats
Centralized systems benefit from network effects that create a competitive moat. In contrast, decentralized systems foster network effects through community participation and shared value creation.
Self-Sovereign Identity (SSI): Reclaiming Digital Personhood
Self-sovereign identity (SSI) represents a paradigm shift in how we manage and perceive digital identities. It empowers users to control their digital presence, deciding what information to share and with whom.
The Problem with Traditional Digital Identity
Traditional digital identity systems are often centralized, making them vulnerable to data breaches and cyber attacks. These systems typically rely on a single authority to manage and verify identities, creating a single point of failure. Moreover, users have limited control over their personal data, often leading to privacy concerns.
Centralized identity management can result in a lack of interoperability between different services, further complicating the digital landscape. Users are required to create multiple accounts and remember various passwords, leading to a fragmented digital identity.
How SSI Works: Technical Foundations
SSI is built on decentralized technologies, primarily blockchain, to provide a secure and user-centric identity management system. Two key components of SSI are Verifiable Credentials and Decentralized Identifiers (DIDs).
Verifiable Credentials
Verifiable Credentials are digital certificates issued by trusted entities that attest to specific attributes or qualifications of an individual or organization. These credentials are tamper-evident and can be verified without relying on the issuer.
Decentralized Identifiers (DIDs)
DIDs are unique identifiers that are not controlled by any single entity. They are created, managed, and used by individuals or organizations directly, without the need for a central authority. DIDs are recorded on a blockchain or other decentralized ledger, ensuring their integrity and availability.

Real-World Applications of Self-Sovereign Identity
SSI has numerous applications across various sectors, including finance, healthcare, and education. For instance, in the financial sector, SSI can simplify Know Your Customer (KYC) processes, reducing costs and enhancing security. In healthcare, SSI can provide patients with control over their medical records, ensuring privacy and facilitating secure sharing with healthcare providers.
The adoption of SSI can lead to a more secure, privacy-centric, and user-friendly digital ecosystem. As the technology continues to evolve, we can expect to see more innovative applications of self-sovereign identity in the future.
Cryptographic Signatures: The Technical Backbone of Web3 Identity
In the realm of Web3, cryptographic signatures play a pivotal role in authenticating identities and transactions. These signatures are the foundation upon which the security and trustworthiness of Web3 interactions are built.
Public-Private Key Infrastructure Explained
The public-private key infrastructure is a cornerstone of cryptographic signatures in Web3. It involves a pair of keys: a public key that is shared openly and a private key that is kept secret. This asymmetric cryptography enables secure authentication and verification of transactions without exposing sensitive information.
The process works as follows:
- A user generates a public-private key pair.
- The public key is used to create a unique address or identity.
- The private key is used to sign transactions, which can then be verified using the public key.
Zero-Knowledge Proofs and Privacy-Preserving Verification
Zero-knowledge proofs (ZKPs) are another crucial element in the cryptographic toolkit of Web3. ZKPs allow one party to prove that a statement is true without revealing any information beyond the validity of the statement itself.
“ZKPs enable privacy-preserving verification, which is essential for maintaining confidentiality in Web3 transactions.”
— Expert in Cryptographic Technologies
For instance, ZKPs can be used to verify identity without disclosing personal details, enhancing privacy and security.
| Feature | Traditional Identity Verification | ZKP-based Verification |
|---|---|---|
| Privacy | Limited | High |
| Security | Variable | Enhanced |
Identity Recovery and Management Challenges
While cryptographic signatures and ZKPs offer robust security, they also introduce challenges, particularly in identity recovery and management.
Social Recovery Systems
Social recovery systems are designed to help users regain access to their identities or assets if they lose their private keys. This involves trusted contacts or guardians who can assist in the recovery process.
Multi-Signature Security
Multi-signature (multisig) wallets require multiple private keys to authorize a transaction, adding an extra layer of security. This approach is particularly useful for organizations or shared accounts.
By understanding and implementing these cryptographic techniques, Web3 can offer a more secure and user-friendly experience.
Decentralized Storage Solutions: IPFS, Filecoin, and Beyond
The rise of decentralized storage solutions marks a significant shift in how data is stored, accessed, and managed. Traditional centralized storage models are being challenged by decentralized alternatives that promise greater security, resilience, and user control.
How IPFS Revolutionizes Content Addressing
IPFS (InterPlanetary File System) is a decentralized storage protocol that revolutionizes content addressing by using a distributed hash table to store and share files across a network of nodes. Unlike traditional HTTP protocols that rely on location-based addressing, IPFS uses content-based addressing, ensuring that files are accessed based on their content rather than their location.
This approach provides several benefits, including:
- Persistent storage: Files remain accessible even if the original host is offline.
- Resilience to censorship: Content is harder to censor as it’s not tied to a specific location.
- Efficient data sharing: Files can be retrieved from multiple sources, reducing bandwidth usage.

Filecoin’s Economic Model for Decentralized Storage
Filecoin builds upon the IPFS protocol by introducing an economic model that incentivizes individuals and organizations to contribute storage capacity to the network. Participants are rewarded with Filecoin tokens for providing storage and retrieving data, creating a robust and decentralized storage marketplace.
| Feature | Filecoin | Centralized Storage |
|---|---|---|
| Storage Provisioning | Decentralized, community-driven | Centralized, controlled by a single entity |
| Economic Incentives | Participants are rewarded with tokens | No direct incentives for storage providers |
Arweave and Permanent Storage Solutions
Arweave offers a unique approach to decentralized storage through its concept of permanent storage. Arweave’s network allows users to store data permanently, with a pay-once, store-forever model that ensures data remains accessible indefinitely.
Pay-Once, Store-Forever Model
Arweave’s economic model is based on a one-time fee that covers the cost of storing data permanently. This is achieved through a novel consensus mechanism called Proof of Access, which ensures that data remains available and is replicated across the network.
Use Cases for Permanent Storage
Permanent storage solutions like Arweave have various applications, including:
- Archiving historical data and documents.
- Storing critical information that requires long-term preservation.
- Creating censorship-resistant repositories of knowledge.
As decentralized storage solutions continue to evolve, they are poised to play a crucial role in shaping the future of data management and access.
Token-Gated Access: New Models for Digital Permissions
As we dive into the world of Web3, token-gated access emerges as a pivotal element in controlling digital permissions. This innovative approach leverages blockchain technology and cryptocurrencies to manage access to digital content, resources, and communities.
NFTs as Access Credentials
Non-Fungible Tokens (NFTs) are being increasingly used as access credentials, providing a secure and unique way to verify ownership and grant permissions. NFTs can represent membership, exclusive content, or specific rights within a community or platform.
Membership and Community Access
NFTs can serve as membership cards, granting holders access to exclusive events, content, or services. This model is particularly popular in online communities, where NFT ownership can unlock special privileges or content.
Tiered Permission Systems
Tiered permission systems can be implemented using NFTs, where different NFTs correspond to different levels of access or privileges. This allows for a nuanced and flexible approach to managing digital permissions.
Soulbound Tokens and Non-Transferable Rights
Soulbound tokens represent a new frontier in token-gated access, where certain rights or credentials are non-transferable and permanently linked to an individual’s identity. This concept is particularly relevant in the context of identity verification and reputation systems.
Implementing Token Gates: Technical Considerations
Implementing token gates requires careful consideration of several technical factors, including smart contract development, wallet integration, and user experience design. Developers must ensure that token gates are secure, user-friendly, and scalable.
By understanding the technical and practical aspects of token-gated access, developers and organizations can unlock new models for digital permissions, enhancing security, and user experience in the Web3 ecosystem.
DAOs: Decentralized Governance and Collective Decision-Making
In the realm of Web3, DAOs have become a crucial element in facilitating decentralized governance and community-driven decision-making. DAOs represent a significant shift from traditional, centralized organizational structures to more democratic and transparent models.
DAO Structure and Operations
A DAO operates through a set of rules encoded as a smart contract on a blockchain, ensuring transparency and immutability. The structure typically involves a community of stakeholders who make decisions collectively through a voting process.
The operational framework of a DAO includes several key components:
- Proposal creation and submission
- Voting mechanisms using governance tokens
- Execution of decisions through smart contracts
Governance Tokens and Voting Mechanisms
Governance tokens are a critical element in DAOs, as they enable participation in the decision-making process. The distribution and management of these tokens can significantly impact the governance structure.
On-Chain vs. Off-Chain Governance
DAOs can implement governance mechanisms either on-chain or off-chain. On-chain governance involves recording all transactions and decisions directly on the blockchain, enhancing transparency and security. Off-chain governance, while potentially more flexible, may compromise on transparency.
Quadratic Voting and Other Novel Systems
Quadratic voting is an innovative approach that aims to mitigate the issue of vote buying and promote more equitable decision-making. Other novel systems, such as liquid democracy, are also being explored to enhance the governance process.
Case Study: Uniswap Governance
Uniswap, a leading decentralized exchange, has implemented a robust governance model through its DAO. The Uniswap governance process involves proposing and voting on changes to the protocol, using UNI tokens for voting.
The success of Uniswap’s governance model can be attributed to its transparent and community-driven approach. It serves as a valuable example for other DAOs looking to establish effective governance structures.

Real-World Examples of Web3 Infrastructure in Action
The practical applications of Web3 infrastructure are diverse, ranging from decentralized domain name systems to social networking protocols. These examples not only demonstrate the versatility of Web3 technologies but also highlight their potential to transform various aspects of the digital world.
ENS: Decentralized Domain Name System
The Ethereum Name Service (ENS) is a critical component of the Web3 ecosystem, providing a decentralized alternative to traditional DNS. ENS allows users to replace complex Ethereum addresses with human-readable names, enhancing usability and accessibility.
Technical Architecture
ENS operates on a system of smart contracts on the Ethereum blockchain. When a user registers a domain, it is recorded on the blockchain, ensuring decentralization and security. The ENS resolver is responsible for translating the human-readable name into the corresponding Ethereum address.
Integration with Traditional DNS
One of the significant advantages of ENS is its potential to integrate with traditional DNS. This interoperability allows for a smoother transition between the centralized and decentralized web, enabling users to access ENS domains through standard web browsers with appropriate configurations.
Filecoin: Incentivized Decentralized Storage
Filecoin is another prominent example of Web3 infrastructure in action. It offers a decentralized storage network where users can rent out their unused storage space in exchange for Filecoin tokens. This creates an incentivized ecosystem for storage providers and a cost-effective solution for those needing storage.
Key Benefits of Filecoin include its decentralized nature, which enhances data security and availability, and its economic model, which incentivizes participation.
Lens Protocol: Decentralized Social Networking
Lens Protocol represents a significant step towards decentralized social networking. By leveraging blockchain technology, Lens Protocol enables users to own and control their social media data, providing a more secure and private alternative to traditional social media platforms.
Decentralized social networking is an area where Web3 can potentially offer substantial improvements over the current centralized models, giving users more control over their data and interactions.
Gitcoin: Funding Public Goods
Gitcoin is a platform that facilitates the funding of public goods and open-source projects through a decentralized mechanism. It connects developers with projects that need funding, often through quadratic funding models that match community contributions with additional funds from larger donors.
The use of quadratic funding in Gitcoin ensures that projects with broad community support receive more substantial funding, aligning the incentives with the community’s interests.
Enterprise Adoption of Web3 Technologies
The adoption of Web3 technologies is gaining momentum among enterprises, driven by the promise of decentralization and enhanced security. As businesses look to innovate and stay competitive, they’re exploring the potential of blockchain, decentralized storage, and other Web3 solutions.
Meta’s Web3 Strategy and Initiatives
Meta is actively integrating Web3 technologies into its platforms, focusing on creating a more decentralized internet. Their initiatives include exploring digital identity solutions and decentralized social networks. By leveraging Web3, Meta aims to give users more control over their data and online interactions.
Google Cloud’s Blockchain Integration
Google Cloud is enhancing its services with blockchain technology, providing a robust infrastructure for Web3 applications. Their efforts include blockchain data analytics and node validation services, making it easier for enterprises to adopt and integrate Web3 solutions.
Traditional Finance Entering the Web3 Space
The traditional finance sector is increasingly entering the Web3 space, recognizing the potential of blockchain and decentralized finance (DeFi). This shift is driven by the need for more efficient, transparent, and secure financial services.
Banking Sector Implementations
Banks are exploring Web3 technologies to improve their services, including cross-border payments and trade finance. By adopting blockchain, banks can reduce transaction costs and enhance security.
Asset Tokenization Platforms
Asset tokenization is another area where traditional finance is intersecting with Web3. Platforms are emerging that allow for the tokenization of real-world assets, providing new investment opportunities and improving liquidity.

As enterprises continue to adopt Web3 technologies, we can expect to see significant advancements in how businesses operate and innovate. The integration of these technologies is set to transform industries, from finance to social media, by providing more secure, transparent, and efficient solutions.
User Benefits of Decentralized Infrastructure
As we move towards a more decentralized internet, users are poised to gain significantly in terms of privacy and control. Decentralized infrastructure is not just a technological shift; it’s a paradigm change that directly benefits users in several key areas.
Enhanced Privacy and Data Protection
One of the most significant advantages of decentralized infrastructure is the enhanced privacy and data protection it offers. By utilizing blockchain technology and other decentralized networks, users can enjoy a level of privacy that is not possible in traditional, centralized systems. Data is no longer stored in a single, vulnerable location, reducing the risk of massive data breaches.
True Digital Ownership and Portability
Decentralized infrastructure empowers users with true digital ownership and portability. Through the use of decentralized identifiers and blockchain-based ownership records, users can truly own their digital assets, such as NFTs, and have the freedom to transfer them across different platforms and services.
Reduced Costs Through Disintermediation
Decentralized infrastructure has the potential to significantly reduce costs for users by cutting out intermediaries. By enabling direct peer-to-peer transactions and interactions, decentralized networks can lower fees associated with traditional, intermediated models.
Censorship Resistance and Freedom of Expression
Another critical benefit of decentralized infrastructure is its resistance to censorship, promoting freedom of expression. Decentralized networks are inherently more resilient to attempts at censorship because data and applications are distributed across a wide network of nodes, making it difficult for any single entity to control or suppress information.
In conclusion, the shift towards decentralized infrastructure promises to bring about a new era of digital rights and freedoms for users, enhancing privacy, ownership, and freedom of expression while reducing costs.
Challenges and Limitations in the Web3 Ecosystem
Despite its potential, the Web3 ecosystem is not without its limitations, facing issues that range from scalability to regulatory hurdles.
Scalability Issues and Technical Bottlenecks
One of the primary challenges facing Web3 is scalability. As the number of users and transactions increases, the network’s ability to process them efficiently becomes a significant issue.
Layer2 Solutions and Rollups
Layer2 solutions and rollups are being developed to address scalability. These technologies enable faster transaction processing by handling transactions off the main blockchain or by bundling multiple transactions into a single transaction.
Sharding and Parallel Processing
Another approach to scalability is sharding, which involves dividing the blockchain into smaller, independent pieces called shards. Each shard can process transactions in parallel, significantly increasing the overall capacity of the network.
Regulatory Uncertainty and Compliance Challenges
Web3 also faces regulatory uncertainty. The lack of clear guidelines and standards for Web3 technologies creates compliance challenges for developers and users alike.
User Experience Barriers to Mainstream Adoption
The user experience in Web3 is often cited as a barrier to mainstream adoption. Complex wallet management and the need for users to understand cryptographic principles can deter non-technical users.
Energy Consumption and Environmental Concerns
Finally, the environmental impact of Web3, particularly the energy consumption associated with certain consensus mechanisms like Proof of Work, is a growing concern. Efforts to transition to more energy-efficient consensus mechanisms, such as Proof of Stake, are underway.
In conclusion, while Web3 holds great promise, it faces significant challenges that must be addressed. By understanding and tackling these issues, we can work towards a more scalable, user-friendly, and sustainable Web3 ecosystem.
The Convergence of AI and Web3
Web3 and AI are merging to create a more decentralized and intelligent internet. This convergence is enabling the development of decentralized AI computation networks, AI-powered smart contracts, and privacy-preserving machine learning on blockchain.
Decentralized AI Computation Networks
Decentralized AI computation networks are being developed to provide a more secure and transparent way of performing AI computations. These networks utilize blockchain technology to enable secure, decentralized, and community-driven AI processing.
Key benefits of decentralized AI computation networks include:
- Increased security through decentralized data storage
- Improved transparency via blockchain-based transaction records
- Community-driven AI model development and validation
AI-Powered Smart Contracts and Oracles
AI-powered smart contracts are enhancing the capabilities of blockchain technology by integrating AI-driven decision-making processes. Oracles, which provide external data to smart contracts, are also being improved with AI to ensure more accurate and reliable data feeds.
| Feature | Traditional Smart Contracts | AI-Powered Smart Contracts |
|---|---|---|
| Decision Making | Predefined rules | AI-driven, adaptive |
| Data Input | Manual or oracle-provided | AI-enhanced oracles for real-time data |
Privacy-Preserving Machine Learning on Blockchain
Privacy-preserving machine learning on blockchain is a critical area of development, enabling the training of AI models on encrypted data without compromising user privacy.
Federated Learning Applications
Federated learning allows for the training of AI models across decentralized data sources without aggregating the data itself, thus preserving privacy.
Data Marketplaces and Monetization
Data marketplaces are emerging, where individuals can monetize their data while maintaining control over its usage through blockchain-based privacy-preserving techniques.
DePIN: Decentralized Physical Infrastructure Networks
DePIN represents a revolutionary shift in how we think about physical infrastructure, leveraging blockchain technology to create decentralized networks. This innovative approach is transforming the way we manage and interact with physical resources.
Tokenizing Real-World Resources
One of the key aspects of DePIN is its ability to tokenize real-world resources. This process involves converting rights to assets into digital tokens on a blockchain, enabling more efficient, secure, and transparent management of resources. Tokenization opens up new opportunities for investment and utilization of physical assets.
Wireless Networks and Connectivity (Helium)
DePIN is being applied in various domains, including wireless networks and connectivity through projects like Helium. Helium’s decentralized network allows individuals to provide and consume wireless coverage, creating a more robust and community-driven connectivity solution. Decentralized wireless networks are poised to revolutionize how we access and share connectivity.
Decentralized Compute Resources
Another significant application of DePIN is in decentralized compute resources. This includes distributed GPU networks and edge computing applications, which are crucial for handling complex computations and reducing latency.
Distributed GPU Networks
Distributed GPU networks enable the sharing and utilization of GPU power across a decentralized network. This is particularly beneficial for applications requiring intense computational power, such as AI and machine learning.
Edge Computing Applications
Edge computing applications, facilitated by DePIN, bring computation closer to the source of data, reducing latency and improving real-time processing capabilities. This is critical for applications like IoT devices and autonomous vehicles.
As DePIN continues to evolve, it promises to unlock new efficiencies and opportunities in the management of physical infrastructure. By decentralizing control and enabling tokenization, DePIN is set to have a profound impact on various industries.
“The decentralized physical infrastructure networks are not just a technological shift; they represent a new economic and social paradigm.”
Conclusion: The Future Landscape of Web3 Infrastructure
The future of Web3 is poised to revolutionize the way we interact with the internet, leveraging decentralized infrastructure and blockchain technology to create a more secure, transparent, and user-centric online ecosystem.
As advancements in blockchain technology continue to emerge, we can expect to see significant improvements in decentralized infrastructure, enabling faster, more secure, and more efficient data management and transactions.
The convergence of Web3 and other technologies, such as AI and DePIN, is expected to unlock new use cases and applications, further driving the adoption of decentralized infrastructure and shaping the future landscape of the internet.
With major players like Meta and Google Cloud exploring Web3 initiatives, the potential for mainstream adoption and innovation in this space is vast, promising a future where users have greater control over their digital identity, data, and assets.
FAQ
What is Web3 and how does it differ from Web2?
Web3 represents a decentralized internet architecture, contrasting with the centralized models of Web2. It leverages blockchain technology, decentralized storage solutions like IPFS, and token-based access systems to give users more control over their data and identity.
How does self-sovereign identity work in Web3?
Self-sovereign identity (SSI) in Web3 allows individuals to manage their digital identity without relying on centralized authorities. It uses verifiable credentials and decentralized identifiers, enabling users to control their personal data and authentication.
What are the benefits of decentralized storage solutions like IPFS and Filecoin?
Decentralized storage solutions like IPFS and Filecoin offer enhanced data security, censorship resistance, and permanence. They distribute data across a network, making it harder to manipulate or delete, and provide economic incentives for storage providers.
How do token-gated access systems work?
Token-gated access systems use digital tokens, such as NFTs or specific cryptocurrencies, to grant access to content, services, or communities. These tokens can represent membership, ownership, or specific rights, and their transfer or possession determines access levels.
What are DAOs and how do they operate?
DAOs, or Decentralized Autonomous Organizations, are entities that operate on blockchain technology, allowing for decentralized governance and decision-making. They use governance tokens and voting mechanisms to enable collective decision-making among members.
How is AI integrating with Web3 technologies?
The integration of AI with Web3 involves using decentralized AI computation networks, AI-powered smart contracts, and privacy-preserving machine learning on blockchain. This convergence aims to enhance the functionality and efficiency of Web3 applications.
What is DePIN and how does it relate to Web3 infrastructure?
DePIN, or Decentralized Physical Infrastructure Networks, refers to the tokenization of real-world resources and infrastructure, such as wireless networks and compute resources, to create decentralized networks. This concept is part of the broader Web3 infrastructure development.
What are the challenges facing the adoption of Web3 technologies?
Challenges include scalability issues, regulatory uncertainty, user experience barriers, and environmental concerns related to energy consumption. Addressing these challenges is crucial for the mainstream adoption of Web3 technologies.
How does Web3 impact data ownership and privacy?
Web3 enhances data ownership and privacy by giving users control over their personal data through self-sovereign identity and decentralized storage. It reduces reliance on centralized entities that can exploit user data.
What are some real-world examples of Web3 infrastructure in action?
Examples include ENS (Ethereum Name Service) for decentralized domain names, Filecoin for incentivized decentralized storage, Lens Protocol for decentralized social networking, and Gitcoin for funding public goods through quadratic funding.